How to Successfully Perform a Security Risk Assessment in Your Company
Following the tendency of digital transformation, companies worldwide face both new opportunities and hurdles to overcome. On one hand, CEOs get new revenue streams, on the other hand, they have to fight off more targeted and sophisticated cyber-attacks, for which highly professional cyber firms are not a problem anymore.
Nearly all C-suite executives from the survey were asked about the core objectives and the majority of them believe their companies will have to cope with severe threats and disruptions in a couple of years. In 2019, 75% of С-level executives named cyber security and technology adoption among their top priorities.

Today cyber attackers are seeking highly profitable ways to breach valuable data, such as intellectual property (IP), health records, personal information, or financial data. Thus, they perform complex and the most dreaded crime strategies such as monetizing data access using ransomware or Distributed Denial of Service (DDoS) attacks. A single malicious email can lead to disruptions in most aspects of business operations.
What Is a Security Risk Assessment?
When it comes to identifying, forecasting, and eliminating any cyber-related threats, security risk assessment comes into play as one of the most vital integral processes in enterprise risk management (ERM). With the accurate risk assessment in place, organizations can:
- Identify risk events and weaknesses
- Determine the possibility cybercrimes will occur
- Predict the impact on business
- Prepare adequate techniques to fight risks
- Establish a risk-aware environment
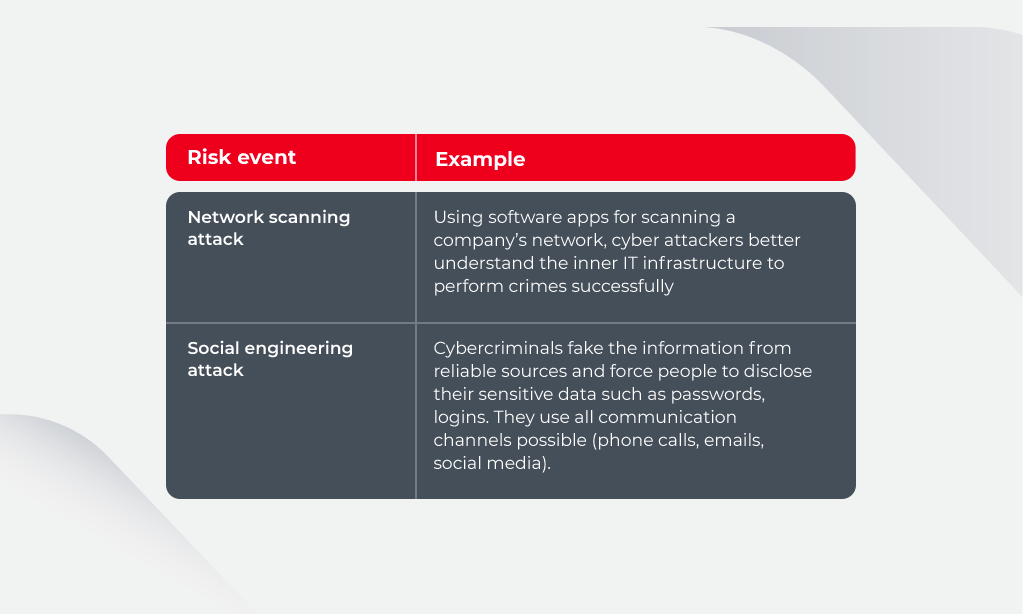
Why Cyber Security Risk Matters
When thinking about how important and valuable the security risk assessment is, take the following figures into consideration:
- 4.1 billion is the number of data records stolen in the first six months of 2019.
- 62% of companies underwent phishing attacks in 2018.
- In the 2005–2018 period there were almost 9,000 breaches recorded.
- 52% of breaches included hacking, 28% malware, and 33% social engineering.
- 300 billion of passwords will be created by 2020, enriching chances of cybercrimes.
Therefore, companies are going to fortify their cyber security, spending on it US$133.7 billion by 2022. Without security risk assessment solutions, you could be exposed to adverse disruptions.

After all, a little time and effort implementing security measures can save your company. Risk assessment has the following benefits:
Prevent cyber crimes and cut costs: In a long-term perspective timely detection, analysis, and management of cybercrimes allow organizations to prevent those attacks that involve huge financial implications.
Detect weak points and eliminate them: Security risk assessment identifies vulnerabilities and inefficiencies in a company’s cyber defense system. This empowers responsible persons to plan an additional budget to fill these gaps. As a result, you have powerful cyber security.

Stay legal and safe: Thanks to regular risk assessment measures, businesses comply with all regulations and international standards. This way, companies reassure customers their data is safe and secure.
Improve visibility and collaboration: Risk assessment involves many departments to collaborate. Thus, communication between employees is high. With enhanced visibility of the IT assets, data, and endpoint hardware, IT personnel can closely monitor and better handle risks.
Prevent risk events: Detecting risk events before they come into effect prevents data breaches. As risks may lead to severe consequences for business, this risk detection will pave the way to integrate robust security controls.
Conducting a Cyber Security Risk Assessment
After all the terrifying statistics on one side and a bunch of benefits on the other side, we’ve got to a brief and step-by-step guideline on how to successfully perform information security risk management within your company. We analyzed plenty of sources and picked the major security risk assessment milestones.

1. Define and prioritize assets. The initial step is to define which assets need to be assessed. These assets may include equipment, a building, or even a worker. Identifying assets will allow you to prioritize them. Depending on the value of an asset, apply evaluation measures.
2. Detect threats and weaknesses. Here you need to detect what can happen (natural disaster, human error, system failure, and more). Afterward, find out the weaknesses inside your company, which can be used by cyber attackers to breach data or harm your defense system.
3. Analyze security measures and add new ones. Analyze on-premise security measures to reduce and mitigate risks and recognize vulnerabilities. These measures may include hardware or software (antivirus) or non-technical controls (physical locks). Monitor the market and adopt new adequate solutions to replace ineffective ones. Below you can see the example of a risk management plan.

4. Find out the possibility of the risk events occurrence. Next, calculate the possibility of cyber risks occurrence along with the consequences. You need to identify when the threat is likely to happen and the level of its success. Then use this data to plan the budget to decrease the likelihood of each risk identified.
5. Rank risks by their cost. Categorizing risks based on their severity (serious, moderate, minor) will help you take actions timely and mitigate really dangerous attacks. Then estimate the costs needed for each risk prevention. If it requires more investment than the asset’s actual value than maybe it is not worthy of being protected.
6. Document the results of risk assessment. By creating a report on your risk assessment efforts, you help management to make decisions on cyber security matters faster and accurately. Ideally, the report should contain all possible threats, the likelihood of the occurrence(s), risk costs, possible measures to be taken in case of cybercrime.
How Blockchain Can Help to Combat Cyber Attacks
Blockchain is an omnipresent tech solution that has a dramatic impact on numerous sectors of digital transformation. Business executives and global organizations like Nasa, for example, integrate Blockchain to boost their cyber security.
This solution hasn’t advanced yet to the utmost degree, nevertheless, Forbes suggests some promising use cases where Blockchain can be seen in action.
Moving to Decentralized Type of Storages
The most convenient thing for cyber adversaries is to keep all of your sensitive data in one place. There is nothing easier than to steal valuable assets from centralized storage. As businesses started to rethink their approaches to cyber security, Blockchain solutions became an option.
For instance, with Blockchain, you create a decentralized data storages. The key to access these repositories can be changed anytime, allowing for much higher protection from criminals in case they get inside. Plus, there won’t be a single place to breach, which minimizes the risk of attack.
Advancing IoT Security
Blockchain can boost IoT solutions with intelligent features to make security decisions autonomous. For instance, devices can recognize malicious nodes without appealing to management and block them respectively.
Another option possible with Blockchain tech is safeguarding all the data interchanges between IoT devices. It provides real-time secure data transferring and ensures instant interaction between devices on huge distances.
Creating More Secure DNS
Domain Name System (DNS) is like a phonebook of the internet, containing the names for all websites, devices, services connected to it. Perpetrators can cause colossal damage by hacking the website’s IP address. They can transfer intended users to a scam resource or crash website. Combining DNS and DDoS attacks, criminals make websites completely unavailable for very long periods.
Again, Blockchain is here helpful with its decentralized nature. Hackers cannot make use of vulnerable points in a network, because the domain information is stored on a distributed ledger permanently, where smart contracts power the connection.

Enhancing Security of Private Conversations
Private messaging has long become a part of trade negotiations, especially if considering social media commerce. This communication between buyers and sellers usually contains a lot of metadata (phone numbers, time the message was sent, location of the sender and receiver), which can be an attraction for cyber scammers.
Many messengers are encrypted but are vulnerable and far from being utterly secure. Nowadays, Blockchain offers solutions to tackle these imperfections and make messaging safe with a unified communication ecosystem. The technology secures all data and enables interaction between various messaging apps.
To sum up, the key benefit of using Blockchain as a cyber security technique is decentralization. When all the sensitive data is stored in multiple repositories, it becomes much more challenging for cyber criminals to use it.
Summary: Boost Cyber Security Most Effectively to Avoid Breaches
What is a security risk assessment? Hopefully, we helped answer this question and pave the way to conducting an effective security risk assessment. Companies simply need to follow an accurate plan. Find our suggestions below to alleviate the entire process.
- First, you need to analyze your assets and decide what needs to be assessed.
- Then, find out what threats are likely to occur (natural disasters, human errors, etc.) and weak spots for the cyber attacks.
- Analyzing in-house security measures will also help recognize working methods and those that need to be renovated or replaced.
- The next step is to decide how possible the risk events are and how likely they are to succeed.
- Ranking risks by the cost of their prevention and value of the vulnerable data will be labor- and cost-effective.
- Document the results of risk assessment. This helps to make decisions on cyber security matters faster and accurately.
Often companies outsource risk assessment teams to solve the security issues most comfortably and quickly. When choosing a third-party organization to cooperate with, consider their experience, seek recommendations, check their achievements. Innovecs is a trusted outsourcing company delivering top-notch solutions in many industries. Reach out to the contact center, and we make the best proposal for you.